I remain attentive to what you deem appropriate to maintain the order of the forum, if you want to Hijack my post and continue in another thread I will follow it. I really want to continue learning@@juankrlos el OP original.
No quiero secuestrar tu publicación. Supongo que estamos en el objetivo del hilo original. Si no está de acuerdo, infórmenos y nos trasladaremos a otro lugar.
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Not found c8 in hvec feeds
- Thread starter juankrlos
- Start date
cayoenrique
Member
- Messages
- 475
I do speak Spanish too, I am from the Caribbean. But forum rules say we should speak in English.
Most forums will allow you to write SMALL questions in your native language if you do as you did, place also an English translation with it. I am not sure what the rules are here. So lets stick to English.
Ohh, regards original objective Not found c8 in hvec feeds.
Unless C0der saw something different, there is no useful crypt8 in the file.
Listen I lost my last antenna with Hurricane Maria. So I have not seen many dump logs lately. It was nice to look at your log post. In fact I wonder is something can be done to improve brute-force.
Most forums will allow you to write SMALL questions in your native language if you do as you did, place also an English translation with it. I am not sure what the rules are here. So lets stick to English.
Ohh, regards original objective Not found c8 in hvec feeds.
Unless C0der saw something different, there is no useful crypt8 in the file.
Listen I lost my last antenna with Hurricane Maria. So I have not seen many dump logs lately. It was nice to look at your log post. In fact I wonder is something can be done to improve brute-force.
Last edited:
dvlajkovic
Member
- Messages
- 498
I cannot receive sat-feeds that Juan can so I've recorded 1 min of a FTA HD channel that broadcasts in HEVC.
Then I've encrypted video and audio PIDs in this recording using CW = FF FF FF FD 00 00 00 00.
VPID 1401
APID 1402
Both files are here for download > link.
(password=www.sat-universe.com)
You will see that it's easy to find C8 in my enc file.
I guess that @juankrlos recorded a feed that, for some unknown reason, does not have any usable C8.
Better luck next time, I'd say.
Then I've encrypted video and audio PIDs in this recording using CW = FF FF FF FD 00 00 00 00.
VPID 1401
APID 1402
Both files are here for download > link.
(password=www.sat-universe.com)
You will see that it's easy to find C8 in my enc file.
I guess that @juankrlos recorded a feed that, for some unknown reason, does not have any usable C8.
Better luck next time, I'd say.
cayoenrique
Member
- Messages
- 475
@all
For the record. We had in the past, and now we are saying, that some providers manipulate the stream so that a minimum or just NO crypt8 be sent. We do not know all the tricks they used.
Encrypting ourself a clear feed, will not help C0der to identify a possible attack method. We do not know what are the tricks used. If anyone upload a link, it needs to be encrypted by the provider.
C0der I know you know this, but here for all again. I can assume sat providers use professional equipment made by many different manufacturers. I can easily assume that we could find some similar features, this may be dues to video standard/specifications. But that most likely we will see extra different tricks added by different manufacturers. Of the extra, the most commonly know is the use of Adaptation Field to send unencrypted pads bytes ( 0xFF). But truly will be nice to inspect a few good samples.
For the record. We had in the past, and now we are saying, that some providers manipulate the stream so that a minimum or just NO crypt8 be sent. We do not know all the tricks they used.
Encrypting ourself a clear feed, will not help C0der to identify a possible attack method. We do not know what are the tricks used. If anyone upload a link, it needs to be encrypted by the provider.
C0der I know you know this, but here for all again. I can assume sat providers use professional equipment made by many different manufacturers. I can easily assume that we could find some similar features, this may be dues to video standard/specifications. But that most likely we will see extra different tricks added by different manufacturers. Of the extra, the most commonly know is the use of Adaptation Field to send unencrypted pads bytes ( 0xFF). But truly will be nice to inspect a few good samples.
I have a second capture of 4GB from which I have extracted a sample with "dvbsnoop -n 10000" so that the binary is smallerFor comparison, it would be nice to have an encrypted HEVC from a different transponder, preferably with a known CW.
video pid = 308
https://mega.nz/file/FuQijT6b#t9twnwVROdJbjTy2N_he9Oa0GnXYRg7xFgMLSfion-w
Full File 4GB not found valid C8
Using payload size: 184
PID 134h B8h-Crypt8: 7a0dc29d1340590d [E] Count:34
PID 134h B8h-Crypt8: 8c62a6f715d0e876 [E] Count:34
PID 134h B8h-Crypt8: 2bf9ff8352007998 [E] Count:34
PID 134h B8h-Crypt8: 326d1d8d60ab2602 [E] Count:20
PID 134h B8h-Crypt8: 73fc7dbb82fab1f5 [E] Count:19
PID 134h B8h-Crypt8: 9b9a5c756632b97d [E] Count:10
PID 134h B8h-Crypt8: f487060a8667fed2 [E] Count:10
PID 134h B8h-Crypt8: da0cd00a67b2fd93 [E] Count:10
PID 134h B8h-Crypt8: 956738e7162be7a4 [E] Count:10
PID 134h B8h-Crypt8: 416f549fc14bfa87 [E] Count:10
PID 134h B8h-Crypt8: cdcca9aea9e93ac0 [E] Count:10
Last edited:
I have more captures, different days and the same result. It doesn't seem like bad luck, rather it seems that some trick was implemented to avoid sending c8I have a second capture of 4GB from which I have extracted a sample with "dvbsnoop -n 10000" so that the binary is smaller
video pid = 308
https://mega.nz/file/FuQijT6b#t9twnwVROdJbjTy2N_he9Oa0GnXYRg7xFgMLSfion-w
Full File 4GB not found valid C8
Using payload size: 184
PID 134h B8h-Crypt8: 7a0dc29d1340590d [E] Count:34
PID 134h B8h-Crypt8: 8c62a6f715d0e876 [E] Count:34
PID 134h B8h-Crypt8: 2bf9ff8352007998 [E] Count:34
PID 134h B8h-Crypt8: 326d1d8d60ab2602 [E] Count:20
PID 134h B8h-Crypt8: 73fc7dbb82fab1f5 [E] Count:19
PID 134h B8h-Crypt8: 9b9a5c756632b97d [E] Count:10
PID 134h B8h-Crypt8: f487060a8667fed2 [E] Count:10
PID 134h B8h-Crypt8: da0cd00a67b2fd93 [E] Count:10
PID 134h B8h-Crypt8: 956738e7162be7a4 [E] Count:10
PID 134h B8h-Crypt8: 416f549fc14bfa87 [E] Count:10
PID 134h B8h-Crypt8: cdcca9aea9e93ac0 [E] Count:10
dvlajkovic
Member
- Messages
- 498
please upload captures in originally recorded size, do not make them smaller
Capture 2 original size: https://mega.nz/file/8z4SiSAT#CQNGKtzQg0Q55u1w6jucY548p7fjSKWjvXyaf5TnyQ8please upload captures in originally recorded size, do not make them smaller
Capture 3: https://mega.nz/file/93wiXCTR#rCWHgMUQCRaJC38e2uAXX15UTEAM3Sz_cya_5uscyqI
cayoenrique
Member
- Messages
- 475
For comparison, it would be nice to have an encrypted HEVC from a different transponder, preferably with a known CW.
I guess the Idea of C0der is to compare different files from different operators. I guess to see if we can expect same behavior always. Or if new features are found.
Regards big or smaller. In my case a 4GB log file is trouble as I have limits on my usage.
In the other hand fir people that have no problem with speed or amount of data, BIGGER means more chance to find crypto8 etc.
Now what is important is for a channel to be complete. At minimum it needs to have the encrypted Stream PID (video/audio)+ its REAL ECM PID. Sure PAT, PMT and SD PIDs are nice to have.
dvbsnoop do a quick analysis only LIVE transponder. You need to have the PCSAT/tuner ready for dvbsnoop to capture its -tsraw data.
Best simple way will be to use oetsdec if you know the SID of the channel. Like I did in
Code:
oetsdec .\capture_HEVC_VPID-33.ts 1 out.tsThen I can go into log.txt and see:
Code:
[Emu] Initial analisys of PAT & PMT data for service id: 001 (001)
[Emu] stream found pmt pid: 0x0020 (0032)
[Emu] stream found pat pid: 0x0000 (0000)
[Emu] stream found ecm pid: 0x1FFF (8191)
[Emu] stream found video pid: 0x0021 (0033)
[Emu] stream found Audio pid count: 0x0002
[Emu] stream found Audio pid: 0x0022 (0034)
[Emu] stream found Audio pid: 0x0023 (0035)
[Emu] stream found caid: 0x2600 (9728)
[Emu] info: FFDecsa parallel mode = 128Sure as you may not have the CSA/ECM Key then no decryption will be follow.
I do not know C0der needs. I assume that if he ask for the smaller file original the 790 MB file was big enough for him. In my case 500MB files are big enough for me. I do prefer 100mgs size.
Let me resume. In general we do not need BIG files, we need them complete. If you already used CSA RBT on BIG file, there is no reason for us to doubt you did or not a good try finding crypt8.
And at the moment I guess C0der seems to find out if all providers have same tricks to hide crypt8. So with the log he needs the CSA KEY that goes with the log.
NOW... In the future there may be exceptions to this suggestions in logs.
Lets say you record an event (FEED) from very Beginning to the END. And you find the so call Crypt8 at the beginning as they say. Well for me can be interesting to watch such a log. What cause shuch good luck in finding that key, If it is the sending of Testing Video Chart? Original quality of video is different? etc.
Dale_para_bajo use to say that best time for recording where at the hour, 5-10 minutes before and 5-10 minutes after. You may have seen this is the time commonly use for advertisement. And between event and commercial there are pauses of black video that most likely produce crypt8.
Anyone got the CW for Capture 2 or 3? @moonbase?
3 packets from capture3 with start indicator set for BF:
Same as binary (1kb):
In input.txt for CudaBiss:
This is what we should decrypt (1kb):
About size:
300 MB should be good.
3 packets from capture3 with start indicator set for BF:
47 41 34 9A 98 46 7C 96 A9 9F 64 B1 29 63 1B D0 27 CF 0E 02 AE D3 0B 59 40 27 4D 4D 9F 1B 19 2A 73 53 9D 13 4F AD 48 81 81 55 4F 1B 99 7C 08 FA D0 F8 FD AF 2A A9 5F 23 79 DC 57 78 A0 84 86 12 07 CD 96 C3 E0 6A 46 BC DD 04 E9 1C 43 34 BB 3E 2D A8 41 12 4A DC 7E 5F 7B 63 6A 1F B0 97 A8 FA 29 F3 24 79 4E 6E 51 91 6A A9 45 97 FF ED 2A 95 E5 83 3C D0 B6 DB 4B 41 59 BC 56 D7 F7 55 30 34 7D E1 DD EE FA 89 DC 34 20 98 EC 2E A2 E0 21 59 32 FF 84 ED 8E C5 0E C0 CB 2D F4 6E 73 9E 67 D5 A6 B1 9A 42 0A 06 EE C4 BE 73 CC 25 DA 43 64 84 7E 82 1C 37 87 B4 59 7F F6 AE D4 4E
47 41 34 94 ED CE 0E E2 71 B0 87 85 75 6D 96 54 F7 2C C9 88 1E E6 3B 27 B3 55 3F DC 51 95 AF 00 B3 B9 18 C8 7C BF 9B D3 8A 11 2D 99 37 6D CD CD AC D3 41 22 8F 44 08 62 72 17 A0 6D 69 F7 8C A9 B9 0B CE 35 4D FA 3A F7 80 72 E3 CD B5 EF D6 7E 0B 2D 5F 04 A6 22 7B 01 66 97 DE 9B EF 56 C4 A2 CC E0 20 C5 C5 33 15 C7 73 E5 74 4F 19 80 07 9E B8 30 BA 6E BA A4 9E EC 22 D0 50 F5 81 17 BF 54 42 53 A4 34 54 39 7F 8F 2E CD 0E 2C 84 39 38 62 8B A3 0E 85 DF 1E F1 86 CE 56 28 EF 7B A9 32 C1 52 8F 96 42 1D 5B F2 A4 F2 B0 D8 D8 ED D5 A9 4C DE 5D ED 6E 26 FE 64 FF 74 29 FE 7A
47 41 34 95 13 40 F9 DB B3 82 F0 6A AE 2A B2 83 D6 8D 24 70 F9 C8 6A 08 65 85 B3 5A 68 02 3D E8 06 1E A4 87 D3 42 D4 33 17 5E F6 64 AB 9C 0B AD 8A 9C 3B EF C5 89 FB A6 A3 D9 CB 7A 0F 7C F9 82 77 A6 92 DE B5 B2 04 37 4B DD 08 69 07 0C 9D A4 34 06 22 5A 3B 0F 76 7D DA E6 84 8E 69 FC E9 4C 61 0A AF 96 CD 3F 2B DF D7 B0 53 8B 55 AD 99 2B 80 2F E5 E6 E4 0E 1B F4 BD 5E 08 32 F7 31 9A 8D E2 F0 2E 4A 4A E0 14 96 1A 64 B8 A3 1E F9 F3 C3 40 BF 63 0C 32 D9 02 F7 E8 8A 8D C4 5B 68 74 03 B0 78 D6 70 F4 D3 55 4A E1 BD AC 37 05 DF AB B2 5A 3E DD A2 C5 73 6C D3 BB CC 29 7ASame as binary (1kb):
In input.txt for CudaBiss:
4741349A98467C96A99F64B129631BD0
47413494EDCE0EE271B08785756D9654
474134951340F9DBB382F06AAE2AB283This is what we should decrypt (1kb):
About size:
300 MB should be good.
Anyone got the CW for Capture 2 or 3? @moonbase?
Not checked for the CW's in the new files uploaded by the OP.
I only checked the 1st file that was uploaded.
dvlajkovic
Member
- Messages
- 498
these are invalid C8 as well as the ones from capture 2
cayoenrique
Member
- Messages
- 475
@fiji
Is a quite forum user. But he does have a few nice tools. An ace up his sleeve. Look at the picture, it his own version.
fiji are you good C programmer? Who build your tools?
dvlajkovic
Member
- Messages
- 498
He just uses hex editor and writes his nickname over other people tools
As for the biss keys, here they are:
Capture 2 CW: 55 6F 13 D7 57 AA A1 A2
Capture 3 CW: 54 61 79 2E 68 03 03 6E
As for the biss keys, here they are:
Capture 2 CW: 55 6F 13 D7 57 AA A1 A2
Capture 3 CW: 54 61 79 2E 68 03 03 6E
Thanks.
Maybe someone can decrypt capture3_C8 for us (same file as above):
tsdec.exe -i capture3_C8 -d "54 61 79 2E 68 03 03 6E 54 61 79 2E 68 03 03 6E" -o capture3_C8_decrypted.ts
Maybe someone can decrypt capture3_C8 for us (same file as above):
tsdec.exe -i capture3_C8 -d "54 61 79 2E 68 03 03 6E 54 61 79 2E 68 03 03 6E" -o capture3_C8_decrypted.ts
klickklack
Senior Member
- Messages
- 1,105
this all fake ,when you seen this test it 1st with RBT2 ,then you see nothing , No Crypt8 insideI have a second capture of 4GB from which I have extracted a sample with "dvbsnoop -n 10000" so that the binary is smaller
video pid = 308
https://mega.nz/file/FuQijT6b#t9twnwVROdJbjTy2N_he9Oa0GnXYRg7xFgMLSfion-w
Full File 4GB not found valid C8
Using payload size: 184
PID 134h B8h-Crypt8: 7a0dc29d1340590d [E] Count:34
PID 134h B8h-Crypt8: 8c62a6f715d0e876 [E] Count:34
PID 134h B8h-Crypt8: 2bf9ff8352007998 [E] Count:34
PID 134h B8h-Crypt8: 326d1d8d60ab2602 [E] Count:20
PID 134h B8h-Crypt8: 73fc7dbb82fab1f5 [E] Count:19
PID 134h B8h-Crypt8: 9b9a5c756632b97d [E] Count:10
PID 134h B8h-Crypt8: f487060a8667fed2 [E] Count:10
PID 134h B8h-Crypt8: da0cd00a67b2fd93 [E] Count:10
PID 134h B8h-Crypt8: 956738e7162be7a4 [E] Count:10
PID 134h B8h-Crypt8: 416f549fc14bfa87 [E] Count:10
PID 134h B8h-Crypt8: cdcca9aea9e93ac0 [E] Count:10
in RBT1 TOOL1 you seen this all FAKEC-8
so Provider maybe already have send C8 or Telefon or on begin of -feed
TS file: C:\!Records\capture2_original_VPID-308.ts
Using all PIDs
Using file limit: 2000 MByte
File length: 4095 MByte
UsingFileLen: 2097152000 bytes
Reading file ...
Searching ...
Using payload size: 184
PID: 134h B8h-Crypt8:7A 0D C2 9D 13 40 59 0D [E] Count:20
PID: 134h B8h-Crypt8:8C 62 A6 F7 15 D0 E8 76 [E] Count:14
PID: 134h B8h-Crypt8:73 FC 7D BB 82 FA B1 F5 [E] Count:11
PID: 134h B8h-Crypt8:2B F9 FF 83 52 00 79 98 [E] Count:10
PID: 134h B8h-Crypt8:32 6D 1D 8D 60 AB 26 02 [E] Count:7
PID: 134h B8h-Crypt8:5E 47 52 D3 64 19 26 4D [E] Count:5
PID: 134h B8h-Crypt8:3B 34 A5 88 BE 93 14 D9 [E] Count:3
PID: 134h B8h-Crypt8:50 DD BC 0D 4B D4 C4 6A [E] Count:3
...
Time for searching Crypt8 = 6 sec.
Search Crypt8 in TS Start
TS file: C:\!Records\capture2_original_VPID-308.ts
Using all PIDs
Using file limit: 4096 MByte
File length: 4095 MByte
UsingFileLen: 4294642226 bytes
Reading file ...
Searching ...
Using payload size: 8
Time for searching Crypt8 = 10 sec.
---------------------------------
Search Crypt8 in TS Start
TS file: C:\!Records\capture2_original_VPID-308.ts
Using all PIDs
Using file limit: 4096 MByte
File length: 4095 MByte
UsingFileLen: 4294642226 bytes
Reading file ...
Searching ...
Using payload size: 8
Using payload size: 16
Using payload size: 24
Using payload size: 32
Using payload size: 40
Using payload size: 48
Using payload size: 56
Using payload size: 64
Using payload size: 72
Using payload size: 80
Using payload size: 88
Using payload size: 96
Using payload size: 104
Using payload size: 112
Using payload size: 120
Using payload size: 128
Using payload size: 136
Using payload size: 144
Using payload size: 152
Using payload size: 160
Using payload size: 168
Using payload size: 176
PID: 134h B0h-Crypt8:98 06 84 83 BA 37 89 0B [E] Count:29
PID: 134h B0h-Crypt8:A3 60 9E FD 81 60 5D 91 [E] Count:29
PID: 134h B0h-Crypt8:7D F3 72 5F DB 7B FF E8 [E] Count:28
PID: 134h B0h-Crypt8:97 2F 40 84 6C AA 0F 66 [E] Count:28
PID: 134h B0h-Crypt8:04 E3 37 92 F5 CB 1E D7 [E] Count:27
PID: 134h B0h-Crypt8:53 B3 54 D4 18 5A 41 BA [E] Count:27
PID: 134h B0h-Crypt8:A3 8C BB CB E1 55 41 CD [E] Count:27
PID: 134h B0h-Crypt8:C9 4F 25 FC E8 B8 49 0F [E] Count:27
...
Using payload size: 184
PID: 134h B8h-Crypt8:8C 62 A6 F7 15 D0 E8 76 [E] Count:33
PID: 134h B8h-Crypt8:2B F9 FF 83 52 00 79 98 [E] Count:32
PID: 134h B8h-Crypt8:7A 0D C2 9D 13 40 59 0D [E] Count:32
PID: 134h B8h-Crypt8:32 6D 1D 8D 60 AB 26 02 [E] Count:20
PID: 134h B8h-Crypt8:73 FC 7D BB 82 FA B1 F5 [E] Count:19
PID: 134h B8h-Crypt8:41 6F 54 9F C1 4B FA 87 [E] Count:10
PID: 134h B8h-Crypt8:76 D9 C5 00 5D C3 05 58 [E] Count:10
PID: 134h B8h-Crypt8:95 67 38 E7 16 2B E7 A4 [E] Count:10
...
Time for searching Crypt8 = 150 sec.
But you see Provider using this
PID: 134h B0h-Crypt8: This table we dont have! But i see no correct C8 in this too!
klickklack
Senior Member
- Messages
- 1,105
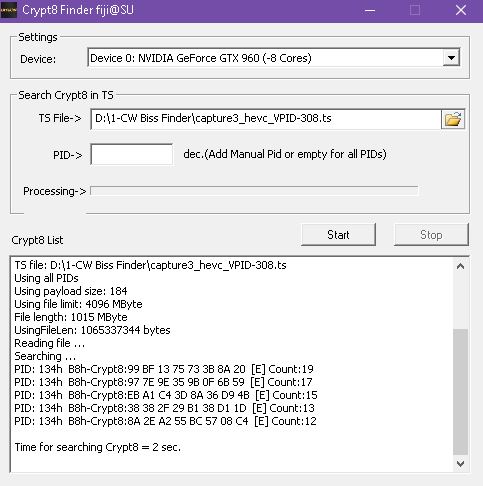
same no crypt inside J:\!Records\capture3_hevc_VPID-308.ts with RBT-V2
only find FAKE-C8 on RBT-V1
TS file: J:\!Records\capture3_hevc_VPID-308.ts
Using all PIDs
Using file limit: 4096 MByte
File length: 1015 MByte
UsingFileLen: 1065337344 bytes
Reading file ...
Searching ...
Using payload size: 184
PID: 134h B8h-Crypt8:99 BF 13 75 73 3B 8A 20 [E] Count:19
PID: 134h B8h-Crypt8:97 7E 9E 35 9B 0F 6B 59 [E] Count:17
PID: 134h B8h-Crypt8:EB A1 C4 3D 8A 36 D9 4B [E] Count:15
PID: 134h B8h-Crypt8:38 38 2F 29 B1 38 D1 1D [E] Count:13
PID: 134h B8h-Crypt8:8A 2E A2 55 BC 57 08 C4 [E] Count:12
Time for searching Crypt8 = 4 sec.
Search Crypt8 in TS Start
TS file: J:\!Records\capture3_hevc_VPID-308.ts
Using all PIDs
Using file limit: 4096 MByte
File length: 1015 MByte
UsingFileLen: 1065337344 bytes
Reading file ...
Searching ...
Using payload size: 8
Time for searching Crypt8 = 1 sec.
only find FAKE-C8 on RBT-V1
TS file: J:\!Records\capture3_hevc_VPID-308.ts
Using all PIDs
Using file limit: 4096 MByte
File length: 1015 MByte
UsingFileLen: 1065337344 bytes
Reading file ...
Searching ...
Using payload size: 184
PID: 134h B8h-Crypt8:99 BF 13 75 73 3B 8A 20 [E] Count:19
PID: 134h B8h-Crypt8:97 7E 9E 35 9B 0F 6B 59 [E] Count:17
PID: 134h B8h-Crypt8:EB A1 C4 3D 8A 36 D9 4B [E] Count:15
PID: 134h B8h-Crypt8:38 38 2F 29 B1 38 D1 1D [E] Count:13
PID: 134h B8h-Crypt8:8A 2E A2 55 BC 57 08 C4 [E] Count:12
Time for searching Crypt8 = 4 sec.
Search Crypt8 in TS Start
TS file: J:\!Records\capture3_hevc_VPID-308.ts
Using all PIDs
Using file limit: 4096 MByte
File length: 1015 MByte
UsingFileLen: 1065337344 bytes
Reading file ...
Searching ...
Using payload size: 8
Time for searching Crypt8 = 1 sec.
klickklack
Senior Member
- Messages
- 1,105
tsdec.exe -i capture3_C8.ts -d "54 61 79 2E 68 03 03 6E 54 61 79 2E 68 03 03 6E" -o capture3_C8_decrypted.tsThanks.
Maybe someone can decrypt capture3_C8 for us (same file as above):
tsdec.exe -i capture3_C8 -d "54 61 79 2E 68 03 03 6E 54 61 79 2E 68 03 03 6E" -o capture3_C8_decrypted.ts
TSDEC: writing decrypted stream to capture3_C8_decrypted.ts
TSDEC: decrypting with constant CW