For the most part this is the same program as before. I only made small changes, changes that we need to move into OpenCL.
For example, removed all unnecessary subroutines and arrays now have dimension of 1. Opencl 1.2 do not allow multidimensional arrays.
des_cscrypt_003.zip (9.75 KB)
Code:
https://workupload.com/file/DbxtzwUDPrU
And I did forgot to post last nist.gov published on DES
Code:
https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-67r2.pdf
I seen no post with questions other that
@Me2019H @K2TSET , so I will just do quick overview
DES is a USA invention, officially published in 1977. Yes very old.
Even when DES Block size is 8 bytes, due to USA Export controls key length was set to ONLY use 56 bits. Transmitted as 8 bytes each with odd parity.
Now DES is strange to me. It is a Block cypher that work in bits. Remember Stream Cypher was the one that works in bits!!
Input Data = Unencrypted Data of 8 Bytes or 64bits.
Output Data = Encrypted Data of 8 Bytes or 64bits.
If you recalled my explanations, Encryption tries to force use of may steps witch only purpose is to require you to spent lots of time. It is this consumption of time that is the base of encryption security. As Brut-force attack will require so much time that you get Old before you get the KEY.
So encryption uses
Loops,
Sboxes and
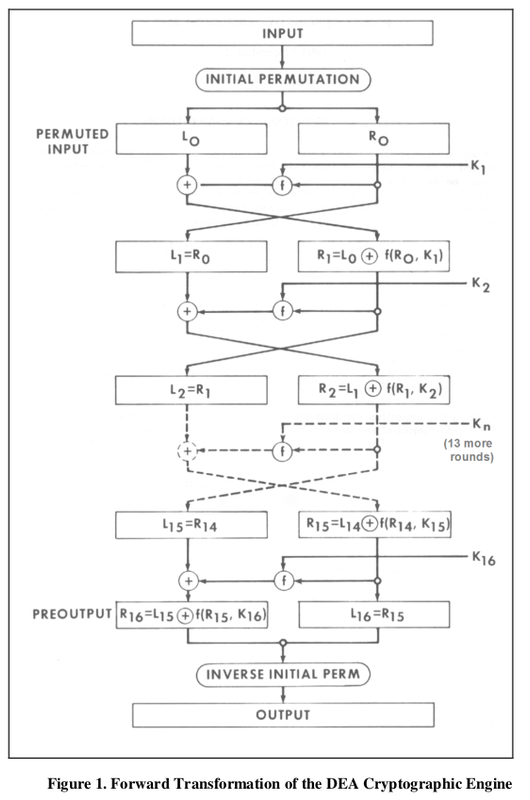
permutations to hide the real value. In the image you may not see the Loop but if you look careful you see it repeats 16 times. On every Iteration it requires 1 key. So again there is a Key schedule process that takes the REAL 56bits Key and uses permutations to create 16 new Keys of size 48 bits. This are K1 --> K16
Now Look carefully. We have 1 Initial permutations of the
Input Data called
Initial Permutation
We have another permutation at the end just before ir returns the
Output Data called
Inverse Initial Permutation
The 64 bit permuted
Input Data is divided in two. The right side register and the left side register.
Encryption is ONLY perform per Iteration on the left side!!
At the end of every Iteration the Left Side is SWAP with the Right side and the process is repeated 16 times.
The basic characteristic of DES encryption is to move bits out of original position. In byte digital programing
Splitting bytes in to bits and moving it bits to other positions, just to recombine in bytes is a process that
takes time.
Now just as a reference. CSA is 48bit and if you can use CUDABIS on one of the latest GPU you could do all test in 1 day.
Now DES Key is 56 bits. This means it has 8 more bits. This 8 bits represent 256 (2^8 =) times harder. In other words you could expect just in this factor that you will required
256 days on best GPU to break DES KEY!!!!
Now DES was created when GPU or even Bitslice was unknown. This makes DES perfect for bitslice as it has no designed protection against such implementation.
Now I would not go into a detail bitslice definition. Use this as refernce, but do not put a lot on effort understanding. Bitslice can be confusing if you do not see it first in use.
Code:
https://usubalang.github.io/usuba/2020/01/14/bitslicing.html
https://timtaubert.de/blog/2018/08/bitslicing-an-introduction/
https://timtaubert.de/blog/2018/08/bitslicing-with-karnaugh-maps/
https://timtaubert.de/blog/2018/08/bitslicing-with-quine-mccluskey/
In a bitsliced implementation, instead of having a single KEY/DATA storing a, say, 64-bit number ( DES=8Byte=64bit), you use instead 64 BS variables. Where BS stand for Bit slice.
Because GPU variables are 32bit long and we used ONLY 1bit, we have then 31 EXTRA bits empty. We can then have 32 Key store on each of our BS variables.
So when we process 1 BS variables we in fact are resolving 32 keys in parallel.
Now the most important aspect of DES bitslice is that, the process is in fact performed in BITS as BS variables contains just 1bit of 32keys!!
NOW PLEASE remember when I say
The basic characteristic of DES encryption is to move bits out of original position. In byte digital programing
Splitting bytes in to bits and moving it bits to other positions, just to recombine in bytes is a process that
takes time.
So here is where we perform MAGIK. If I remove Splitting bytes in to bits and moving it bits to other positions, because BS variables are already bits, then I also remove
takes time. !!! So bitslice then is FASTER.
What all this means? Just as with CSA I do not have on hand a DES OpenCL program. But we can build it if you give me a few days.
Soon I will provide you with a OpenCl program base on des_cscrypt_003, It should be slow as des_cscrypt_003 reads to many tables. Reading memory is a slow process in GPU.
After that we will try to create a DES using bitslice. This is where I will prove that we will NOT need
256 days on best GPU to break DES KEY. My best guess around 15 days. Hey do not complain. That is better than what you have now, witch is no tool, witch mean you can do it in
NEVER time.