You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Understanding CSA
- Thread starter cayoenrique
- Start date
cayoenrique
Senior Member
- Messages
- 489
@all
As I am not 100% here, been busy. I suggest you use symbol at : " @ " before the name. I think in this way it will show as an alert. If not then the most common way for the alert is to quote.
@John448
I see you are new at the forum. Some suggestions:
1rst read the forum general Rules click to read
Beware that different sections have different rules, read them. For example Keys should only be at Key area, or no chat on key area.
As courtesy, It is common for new users to place 1rst post in Introduce Yourself at least just say high happy to be here.
The sample code there is in csasample.zip I will upload here bellow
This is where we are wrong.
Lets start by referencing DES encryption.
DES has a 64-bit word size
DES encryption is performed on also in 64-bit block size = 8 bytes.
So for DES you could have a program just like you ask.
Now CSA is different. While for the most part you could say
CSA has a 64-bit word size
CSA encryption in general is designed for 23 x 64-bit block size. about 184 bytes or 1472-bit!!, now due to adaptation fild that can change for, 0 to 23 blocks of encryption.
Now lets go to the minimum we can have, Here lets look at decryption.

As the drawing shows the minimum required we can have to decrypt is 2 encrypted blocks in this case SB0+SB1. After decryption we can have 1 Clear Text Block DB0.
Now for Encryption is more complex. See

This will depend on Adaptation filed. In general As the drawing shows the minimum required we can have to encrypt is to have ALL 23 Clear DATA or from DB0 to DB22. So that after encryption we could have 1 Clear DATA SB0.
As you see you can not have a simple 64 bit to 64 bit encryption / decryption program. Hope I have clear your question.
As I am not 100% here, been busy. I suggest you use symbol at : " @ " before the name. I think in this way it will show as an alert. If not then the most common way for the alert is to quote.
@John448
I see you are new at the forum. Some suggestions:
1rst read the forum general Rules click to read
Beware that different sections have different rules, read them. For example Keys should only be at Key area, or no chat on key area.
As courtesy, It is common for new users to place 1rst post in Introduce Yourself at least just say high happy to be here.
Start by reading https://www.sat-universe.com/index.php?threads/understanding-csa.319490/post-2037236470John448 said:Could you write a program to encode a plain text?!...
The sample code there is in csasample.zip I will upload here bellow
John448 said:...The program will prompt to input: plaintext (64bit) and key (64bit)
and display: cypher text.
This is where we are wrong.
Lets start by referencing DES encryption.
DES has a 64-bit word size
DES encryption is performed on also in 64-bit block size = 8 bytes.
So for DES you could have a program just like you ask.
Now CSA is different. While for the most part you could say
CSA has a 64-bit word size
CSA encryption in general is designed for 23 x 64-bit block size. about 184 bytes or 1472-bit!!, now due to adaptation fild that can change for, 0 to 23 blocks of encryption.
Now lets go to the minimum we can have, Here lets look at decryption.

As the drawing shows the minimum required we can have to decrypt is 2 encrypted blocks in this case SB0+SB1. After decryption we can have 1 Clear Text Block DB0.
Now for Encryption is more complex. See

This will depend on Adaptation filed. In general As the drawing shows the minimum required we can have to encrypt is to have ALL 23 Clear DATA or from DB0 to DB22. So that after encryption we could have 1 Clear DATA SB0.
As you see you can not have a simple 64 bit to 64 bit encryption / decryption program. Hope I have clear your question.
Attachments
sarfrazali
Registered
- Messages
- 14
csasample.zip send password
csasample.zip send password
Post#1 in page #1 read carefully
cayoenrique
Senior Member
- Messages
- 489
@all
Sorry for the password Issue. I should not upload to SU files withs PASS, there is no need.
I use password for all files I upload to share hosts. Files with pass used to last longer!.
Now Most important is for you to know that I ONLY use ONE password for all my files
Pass:www.sat-universe.com
No need to remeber, when need it, just look at our SU forum core main address www.sat-universe.com
Sorry for the password Issue. I should not upload to SU files withs PASS, there is no need.
I use password for all files I upload to share hosts. Files with pass used to last longer!.
Now Most important is for you to know that I ONLY use ONE password for all my files
Pass:www.sat-universe.com
No need to remeber, when need it, just look at our SU forum core main address www.sat-universe.com
Thanks @cayoenrique for so thorough response. More/less I understand your response.@all
As I am not 100% here, been busy. I suggest you use symbol at : " @ " before the name. I think in this way it will show as an alert. If not then the most common way for the alert is to quote.
@John448
I see you are new at the forum. Some suggestions:
1rst read the forum general Rules click to read
Beware that different sections have different rules, read them. For example Keys should only be at Key area, or no chat on key area.
As courtesy, It is common for new users to place 1rst post in Introduce Yourself at least just say high happy to be here.
Start by reading https://www.sat-universe.com/index.php?threads/understanding-csa.319490/post-2037236470
The sample code there is in csasample.zip I will upload here bellow
This is where we are wrong.
Lets start by referencing DES encryption.
DES has a 64-bit word size
DES encryption is performed on also in 64-bit block size = 8 bytes.
So for DES you could have a program just like you ask.
Now CSA is different. While for the most part you could say
CSA has a 64-bit word size
CSA encryption in general is designed for 23 x 64-bit block size. about 184 bytes or 1472-bit!!, now due to adaptation fild that can change for, 0 to 23 blocks of encryption.
Now lets go to the minimum we can have, Here lets look at decryption.
As the drawing shows the minimum required we can have to decrypt is 2 encrypted blocks in this case SB0+SB1. After decryption we can have 1 Clear Text Block DB0.
Now for Encryption is more complex. See
This will depend on Adaptation filed. In general As the drawing shows the minimum required we can have to encrypt is to have ALL 23 Clear DATA or from DB0 to DB22. So that after encryption we could have 1 Clear DATA SB0.
As you see you can not have a simple 64 bit to 64 bit encryption / decryption program. Hope I have clear your question.
While I didn't have a problem to compile csa_decrypt_1block program in Linux, I get an error when I try to compile code from csasample.
So, I renew my request (with some corrections):
Could you write a very simple program to encrypt payload (184 bites) and display cypher text?
Let's say by default it will use key 0000000000000101 and payload 00 00 00 00 00 00 00 00 00 00 00...
The program could be launch with two parameters -key -payload
cayoenrique
Senior Member
- Messages
- 489
What about a text file with the settings: first line: key, below payload.@John448
There is no simple way. Your request will ask some one to type 184 bytes without making a mistake. Sure I can build one. At the moment I have no AC Power, I will do it latter as soon as power comes back..
I understand there are 281474976710656 possible keys which payload can be encoded with. The result will be 281474976710656 unique encrypted 8 bytes first blocks. Is that right?
Are the first 6 bytes of the cipher text (of the first block) unrepeatable? (that's 281474976710656 possible combination). In other words can the first 6 bytes of the cypher text (of the first block) be the same for two or more keys?
cayoenrique
Senior Member
- Messages
- 489
@John448
Can you tell us about you?
Windows or Linux user, I guess you are Linux user.
Your programing experience.
If you do not seems to have programing skills, how is that you are interested in details?
CSA have a Block Cypher and a Stream Cypher.
Block Cypher
A block cipher is a deterministic algorithm that operates on fixed-length groups of bits. I will add that given a particular Clear Data, every Key will produce a UNIQUE encrypted Data.
A deterministic algorithm is an algorithm that, given a particular input, will always produce the same output.
Now lets look at image again

In general, crypt8 is define by colibri as the 8 bytes produce for a 184 sequence bytes of 0x00 or 0xFF. Lets ignore this fact. and just call crypt8 to the 1rst encrypted 8 byte block or (SB0).
If DB0->DB23 are FIX ( do not change )
Now I can conclude:
that for a Given FIX Clear data DB0 -- DB23, Every different KEY will encrypt into a UNIQUE Crypt8 ( SB0).
But... Clearly if you change any one of the Clear DATA DB0 -- DB23 , the result will change, and as consequence you can have different Keys that produce same Crypt8 (SB0), or NOT unique.
“Unless you people see signs and wonders,” Jesus told him, “you will never believe.”
More simple to understand. A particular REAL Crypt8 can result in two different KEYS one for 0xFF and a different for 0x00.
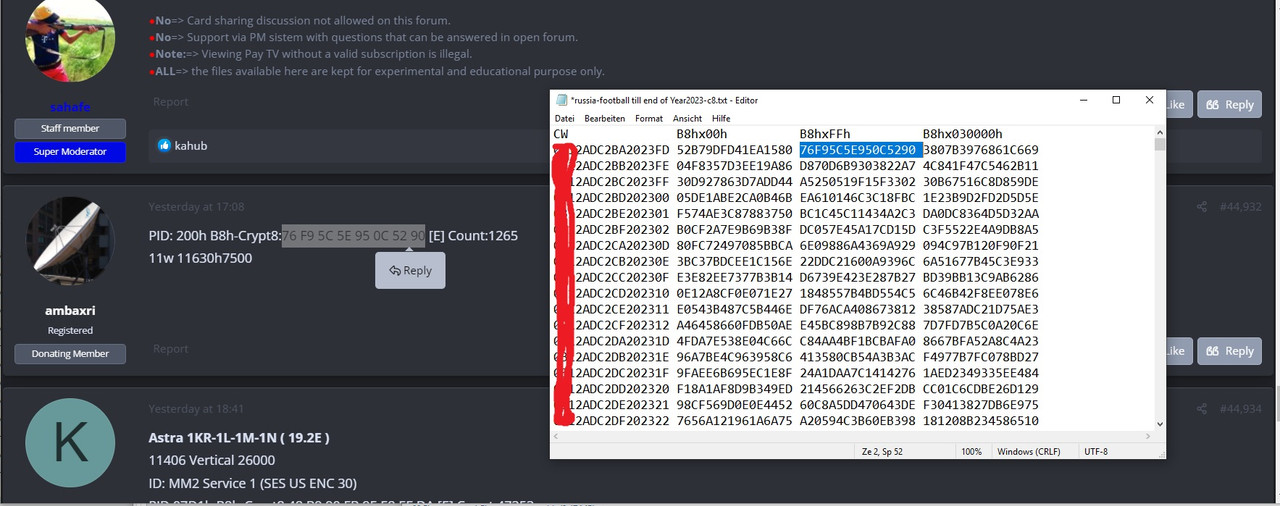
Or even 1 Key can produce diferent crypt8. Juts look at this posted image at https://www.sat-universe.com/index....ols-cw-c-8-update-list.318023/post-2037262712
Can you tell us about you?
Windows or Linux user, I guess you are Linux user.
Your programing experience.
If you do not seems to have programing skills, how is that you are interested in details?
CSA have a Block Cypher and a Stream Cypher.
Block Cypher
A block cipher is a deterministic algorithm that operates on fixed-length groups of bits. I will add that given a particular Clear Data, every Key will produce a UNIQUE encrypted Data.
A deterministic algorithm is an algorithm that, given a particular input, will always produce the same output.
Now lets look at image again

In general, crypt8 is define by colibri as the 8 bytes produce for a 184 sequence bytes of 0x00 or 0xFF. Lets ignore this fact. and just call crypt8 to the 1rst encrypted 8 byte block or (SB0).
If DB0->DB23 are FIX ( do not change )
Now I can conclude:
that for a Given FIX Clear data DB0 -- DB23, Every different KEY will encrypt into a UNIQUE Crypt8 ( SB0).
But... Clearly if you change any one of the Clear DATA DB0 -- DB23 , the result will change, and as consequence you can have different Keys that produce same Crypt8 (SB0), or NOT unique.
“Unless you people see signs and wonders,” Jesus told him, “you will never believe.”
More simple to understand. A particular REAL Crypt8 can result in two different KEYS one for 0xFF and a different for 0x00.
Or even 1 Key can produce diferent crypt8. Juts look at this posted image at https://www.sat-universe.com/index....ols-cw-c-8-update-list.318023/post-2037262712

Last edited:
I don't have much programming experience - very basic. I'm familiar with all common operating systems (Linux, Mac OS, Window)@John448
Can you tell us about you?
Windows or Linux user, I guess you are Linux user.
Your programing experience.
If you do not seems to have programing skills, how is that you are interested in details?
More simple to understand. A particular REAL Crypt8 can result in two different KEYS one for 0xFF and a different for 0x00.
Or even 1 Key can produce diferent crypt8. Juts look at this posted image at https://www.sat-universe.com/index....ols-cw-c-8-update-list.318023/post-2037262712
I'm asking out of curiosity - just want to understand how it works.
In rainbow tables editor I get these results (for xFF payload):
Key: Crypt8:
EEEEEEFFFFFF 23 D1 67 28 63 B6 7C 04
EEEEEEFFFFFE 1D 7B AA 15 B8 63 77 F3
000000000001 D9 02 25 8B 68 6F 9C 15
000000000002 F0 F8 FE 39 FE 70 13 11
000000000003 97 97 30 57 BD 88 79 0A
I was just wondering what kind of results will I get if I change only one byte in payload.
cayoenrique
Senior Member
- Messages
- 489
In general most encryption protocols will prevent anyone from guessing by simple changes.
So it is to expect that changing just one bit will result in maximun bit changes at encryption or decryption.
Ok here is the program requested.
You did not saw that I posted in previous post
John 4:48 "Unless you people see signs and wonders,” Jesus told him, “you will never believe."
So it is to expect that changing just one bit will result in maximun bit changes at encryption or decryption.
Ok here is the program requested.
You did not saw that I posted in previous post
John 4:48 "Unless you people see signs and wonders,” Jesus told him, “you will never believe."
Attachments
cayoenrique
Senior Member
- Messages
- 489
John448
In recent years the process of selecting a new Algo is performed under a contest where a big pot of $$ is offered. Then the best of the best minds in universities will submit their own personal work. Work that in many times have taken years of planing. See for this so called Intellectual wining the contest gave them more ranking in their filed. And as most are professor of Universities they too have knowledge of common hacking procedures.
At the end you can not expect that this so called experts will ignore simple hacks.
Now the reason that Today we have a chance to break some of the codes is not because they can be hack but that recent technology in particular procesors/memories etc are so powerful that suddenly the impossible can be reach.
Now the exception is powervu. I do not know who 1rst found that consecutive "0" in clear data will create a repetitive encrypted sequence. I like most here, we found this at the end of the last decade. But it seems master colibri posted his pdfs in early 2010th. The assembly code was posted by colibry. And as most of us had no knowledge of assembly, it was ignore by the community. In 2014 some people where involved in PowerVu Logging Project . In 2015 master jvvh5897 posted a C version of the Assembly code. He called the cfying program. Then from there most of us started to play with powervu. Just look at first pages of https://www.sat-universe.com/index.php?threads/powervu-chat-only-chat-don‘t-post-keys-here.278286/
In conclusion, you will not find simple ways to hack CSA nor other algos. But it does not mean that we can not find some weird hack. A weird hack that no one thought but that can be a simple thing. I do not know if I am making sense.
I mean stop hopping to find a common simple hack. But PLEASE keep looking for not common ways that no one else thought, as sample old forgotten papers can provide good ideas. Problem is that this professors seems to write in none common language. Papers are not easy to understand.
In recent years the process of selecting a new Algo is performed under a contest where a big pot of $$ is offered. Then the best of the best minds in universities will submit their own personal work. Work that in many times have taken years of planing. See for this so called Intellectual wining the contest gave them more ranking in their filed. And as most are professor of Universities they too have knowledge of common hacking procedures.
At the end you can not expect that this so called experts will ignore simple hacks.
Now the reason that Today we have a chance to break some of the codes is not because they can be hack but that recent technology in particular procesors/memories etc are so powerful that suddenly the impossible can be reach.
Now the exception is powervu. I do not know who 1rst found that consecutive "0" in clear data will create a repetitive encrypted sequence. I like most here, we found this at the end of the last decade. But it seems master colibri posted his pdfs in early 2010th. The assembly code was posted by colibry. And as most of us had no knowledge of assembly, it was ignore by the community. In 2014 some people where involved in PowerVu Logging Project . In 2015 master jvvh5897 posted a C version of the Assembly code. He called the cfying program. Then from there most of us started to play with powervu. Just look at first pages of https://www.sat-universe.com/index.php?threads/powervu-chat-only-chat-don‘t-post-keys-here.278286/
In conclusion, you will not find simple ways to hack CSA nor other algos. But it does not mean that we can not find some weird hack. A weird hack that no one thought but that can be a simple thing. I do not know if I am making sense.
I mean stop hopping to find a common simple hack. But PLEASE keep looking for not common ways that no one else thought, as sample old forgotten papers can provide good ideas. Problem is that this professors seems to write in none common language. Papers are not easy to understand.
