You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Hacking CA system challenge *Tandberg [ NO Keys Allowed in Chat Section/s ]*
- Thread starter Colibri.DVB
- Start date
ELECTRIK DZ
VIP
- Messages
- 1,333
impossible man
why imopssible
dale_para_bajo
Well Known Member
- Messages
- 646
I will like to give it a try the ECM Bruteforce on a channel that fail poc.exe. At least I can say I did not see x83 on a 24 hour period of recording.
I can only set my hands on 58W-3785-H. So here is my recording log of about 12 sec ts.
http://www78.zippyshare.com/v/q4hOyKhe/file.html
SO I ran those 12 seconds with CSA-Rainbow-Table-Tool and got Crypt8
For crypt8 see => http://www.sat-universe.com/showpost.php?p=2036684527&postcount=20516
Can some one be kind to provide solution Thanks ahead.
PD:Sorry I moved crypt8 to it real place.
I can only set my hands on 58W-3785-H. So here is my recording log of about 12 sec ts.
http://www78.zippyshare.com/v/q4hOyKhe/file.html
SO I ran those 12 seconds with CSA-Rainbow-Table-Tool and got Crypt8
For crypt8 see => http://www.sat-universe.com/showpost.php?p=2036684527&postcount=20516
Can some one be kind to provide solution Thanks ahead.
PD:Sorry I moved crypt8 to it real place.
Last edited:
I will like to give it a try the ECM Bruteforce on a channel that fail poc.exe. At least I can say I did not see x83 on a 24 hour period of recording.
I can only set my hands on 58W-3785-H. So here is my recording log of about 12 sec ts.
http://www78.zippyshare.com/v/q4hOyKhe/file.html
SO I ran those 12 seconds with CSA-Rainbow-Table-Tool and got Crypt8
For crypt8 see => http://www.sat-universe.com/showpost.php?p=2036684527&postcount=20516
Can some one be kind to provide solution Thanks ahead.
PD:Sorry I moved crypt8 to it real place.
All CWs were found and sent to your inbox :thum:
@MaRwAn26
It is not my intention to contradict you. I may understand that for crypt8 purpose what I did submitted previous could be enough.
But since I will be using this to do bruteforce I think I need a file with enough EMM information as to get what I will need in the future to get to the real ECM Key. Previous file had only part of key tables.
Now I am new with this crypto8
Here is what program V1.3 shows. I do not know what order this follows. I think I need the solutions of the last crypt8 in order to warranty that y have the whole EMM massages.
PID: C9h Crypt8:AD 13 52 AE 9B 81 72 FB [O] Count:4295
PID: C9h Crypt80 CF DE 2B 21 E0 DE 75 [E] Count:3931
PID: C9h Crypt8:0C FF 10 0B 62 89 CC FE [E] Count:3776
PID: C9h Crypt8:F6 50 A9 F2 29 71 CC 44 [E] Count:3736
PID: C9h Crypt8:09 91 3E FB 89 BD D6 3A [O] Count:3712
PID: C9h Crypt8:77 70 C9 30 74 A6 A1 F4 [E] Count:3586
PID: C9h Crypt87 C2 C5 22 AC DB D6 8E [E] Count:3388
PID: C9h Crypt8:CC 1A 54 09 38 E9 A4 CB [O] Count:3281
...
PID: 12Dh Crypt8:67 82 E5 65 FC 97 41 3F [O] Count:3095
PID: 12Dh Crypt8:02 E3 C1 3F 1B 23 4C DF [E] Count:2371
PID: 12Dh Crypt8:B9 76 D9 D5 E9 A5 83 85 [E] Count:2340
PID: 12Dh Crypt8F 82 76 B1 F2 94 16 E9 [O] Count:2264
PID: 12Dh Crypt8:7F 72 59 B7 F0 BB 45 FF [O] Count:2219
PID: 12Dh Crypt8:E0 F1 6E A7 E8 6C C2 9E [E] Count:2187
PID: 12Dh Crypt8:E7 F7 B8 01 9B 2B 2C 95 [O] Count:2066
PID: 12Dh Crypt8:76 1B CF 3D 63 C4 8A 15 [O] Count:1969
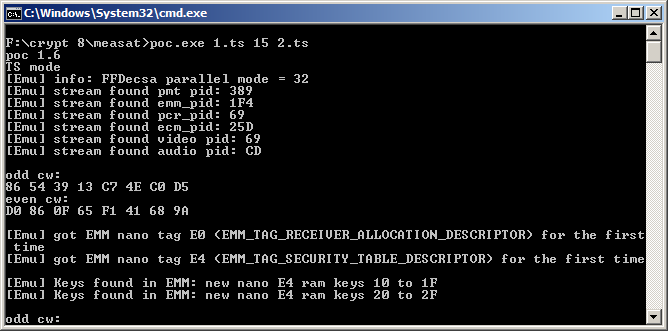
Just for the record this is what poc1.6 shows with the ram keys.
Code:poc 1.6 TS mode [Emu] info: FFDecsa parallel mode = 32 [Emu] stream found pmt pid: C8 [Emu] stream found emm_pid: 1F4 [Emu] stream found pcr_pid: C9 [Emu] stream found ecm_pid: 385 [Emu] stream found video pid: C9 [Emu] stream found audio pid: CB [Emu] got EMM nano tag E0 (EMM_TAG_RECEIVER_ALLOCATION_DESCRIPTOR) for the first time [Emu] active entitlement: B [Emu] got EMM nano tag E4 (EMM_TAG_SECURITY_TABLE_DESCRIPTOR) for the first time [Emu] Keys found in EMM: new nano E4 ram keys 20 to 2F [Emu] Keys found in EMM: new nano E4 ram keys 30 to 3F [Emu] Keys found in EMM: new nano E4 ram keys 0 to F [Emu] Keys found in EMM: new nano E4 ram keys 10 to 1F [Emu] Keys found in EMM: new nano E4 ram keys 20 to 2F [Emu] Keys found in EMM: new nano E4 ram keys 30 to 3F [Emu] Keys found in EMM: new nano E4 ram keys 0 to F [Emu] Keys found in EMM: new nano E4 ram keys 10 to 1F [Emu] Keys found in EMM: new nano E4 ram keys 20 to 2F
Listen I am just experimenting. I am not sure what I will be really needing. But it is better be safe.
So my thanks ahead to you and any one else that show up.
Could you show us in details how to use these CWs keys when found from the crypt8 you provided to get the ECM keys ?
so far I sent you 4 CWs of these C8
C3 66 38 C6 5D 49 5D 03 #[E] PID:00C9h
57 D9 F7 25 5F AC E5 6B #[O] PID:00C9h
CE 4D E7 11 C0 C9 69 0E #[E] PID:012Dh
44 B6 3C B6 37 CE 65 94 #[O] PID:012Dh
also in your *ts file there 2 video programs(1 & 2)
prog1
Code:
poc 1.6
TS mode
[Emu] info: FFDecsa parallel mode = 32
[Emu] stream found pmt pid: C8
[Emu] stream found emm_pid: 1F4
[Emu] stream found pcr_pid: C9
[Emu] stream found ecm_pid: 385
[Emu] stream found video pid: [B][COLOR="Red"]C9[/COLOR][/B]
[Emu] stream found audio pid: CB
[Emu] got EMM nano tag E0 (EMM_TAG_RECEIVER_ALLOCATION_DESCRIPTOR) for the first time
[Emu] active entitlement: B
[Emu] got EMM nano tag E4 (EMM_TAG_SECURITY_TABLE_DESCRIPTOR) for the first time
[Emu] Keys found in EMM: new nano E4 ram keys 20 to 2F
[Emu] Keys found in EMM: new nano E4 ram keys 30 to 3Fprog2
Code:
poc 1.6
TS mode
[Emu] info: FFDecsa parallel mode = 32
[Emu] stream found pmt pid: 12C
[Emu] stream found emm_pid: 1F4
[Emu] stream found pcr_pid: 12D
[Emu] stream found ecm_pid: 386
[Emu] stream found video pid: [B][COLOR="Red"]12D[/COLOR][/B]
[Emu] got EMM nano tag E0 (EMM_TAG_RECEIVER_ALLOCATION_DESCRIPTOR) for the first time
[Emu] active entitlement: C
[Emu] got EMM nano tag E4 (EMM_TAG_SECURITY_TABLE_DESCRIPTOR) for the first time
[Emu] Keys found in EMM: new nano E4 ram keys 20 to 2F
[Emu] Keys found in EMM: new nano E4 ram keys 30 to 3F
Last edited:
satelitindonesia
Senior Member
- Messages
- 336
why, odd cw found but ecm key not found? no one can explain?
file ts - 091.5°E - 3919 H 18385 - RTM SD5
_https://mega.nz/#!LVpSmBxB!mkmuMcFROXGSxfdECEMj3Nsq6LLo8xX0qkMhgLc9-TA

file ts - 091.5°E - 3919 H 18385 - RTM SD5
_https://mega.nz/#!LVpSmBxB!mkmuMcFROXGSxfdECEMj3Nsq6LLo8xX0qkMhgLc9-TA
I attached all the CWs keys here
C3 66 38 C6 5D 49 5D 03 #[E] PID:00C9h
57 D9 F7 25 5F AC E5 6B #[O] PID:00C9h
CE 4D E7 11 C0 C9 69 0E #[E] PID:012Dh
44 B6 3C B6 37 CE 65 94 #[O] PID:012Dh
PID: C9h Crypt8:AD 13 52 AE 9B 81 72 FB [O] Count:4295
PID: C9h Crypt8: D0 CF DE 2B 21 E0 DE 75 [E] Count:3931
PID: C9h Crypt8:0C FF 10 0B 62 89 CC FE [E] Count:3776
PID: C9h Crypt8:F6 50 A9 F2 29 71 CC 44 [E] Count:3736
PID: C9h Crypt8:09 91 3E FB 89 BD D6 3A [O] Count:3712
PID: C9h Crypt8:77 70 C9 30 74 A6 A1 F4 [E] Count:3586
PID: C9h Crypt8: D7 C2 C5 22 AC DB D6 8E [E] Count:3388
PID: C9h Crypt8:CC 1A 54 09 38 E9 A4 CB [O] Count:3281
...
PID: 12Dh Crypt8:67 82 E5 65 FC 97 41 3F [O] Count:3095
PID: 12Dh Crypt8:02 E3 C1 3F 1B 23 4C DF [E] Count:2371
PID: 12Dh Crypt8:B9 76 D9 D5 E9 A5 83 85 [E] Count:2340
PID: 12Dh Crypt8: DF 82 76 B1 F2 94 16 E9 [O] Count:2264
PID: 12Dh Crypt8:7F 72 59 B7 F0 BB 45 FF [O] Count:2219
PID: 12Dh Crypt8:E0 F1 6E A7 E8 6C C2 9E [E] Count:2187
PID: 12Dh Crypt8:E7 F7 B8 01 9B 2B 2C 95 [O] Count:2066
PID: 12Dh Crypt8:76 1B CF 3D 63 C4 8A 15 [O] Count:1969
password will be sent by pm for those who are interested
19 CWs were found :thum: by using V1 and V2
Regards !!!
Last edited:
ViaHussun
Donating Member
- Messages
- 4,098
why, odd cw found but ecm key not found? no one can explain?

file ts - 091.5°E - 3919 H 18385 - RTM SD5
_https://mega.nz/#!LVpSmBxB!mkmuMcFROXGSxfdECEMj3Nsq6LLo8xX0qkMhgLc9-TA
big record upload please
150 or 200 mb
My self comfiled oscam_emu version with powervu and tandberg support.
oscam-svn11268-mipsoe20-webif-libusb-oscam-emu-patched for enigma2 boxes
http://s000.tinyupload.com/?file_id=05455750146573964752
Tandberg config:
===============
Keys in SoftCam.Key:
T <entitlement> 01 <key>
for example (entitlement = 1234):
T 00001234 01 1122334455667788
leading zeros maybe be skipped. same key as above:
T 1234 01 1122334455667788
AU keys:
T <key index (hex)> MK <key>
64 keys are needed:
T 40 MK 1122334455667788
T 41 MK 1122334455667788
...
T 7F MK 1122334455667788
My question is how to find entitlement of channel?
Sent from my SM-N9005 using Tapatalk
oscam-svn11268-mipsoe20-webif-libusb-oscam-emu-patched for enigma2 boxes
http://s000.tinyupload.com/?file_id=05455750146573964752
Tandberg config:
===============
Keys in SoftCam.Key:
T <entitlement> 01 <key>
for example (entitlement = 1234):
T 00001234 01 1122334455667788
leading zeros maybe be skipped. same key as above:
T 1234 01 1122334455667788
AU keys:
T <key index (hex)> MK <key>
64 keys are needed:
T 40 MK 1122334455667788
T 41 MK 1122334455667788
...
T 7F MK 1122334455667788
My question is how to find entitlement of channel?
Sent from my SM-N9005 using Tapatalk
ViaHussun
Donating Member
- Messages
- 4,098
why, odd cw found but ecm key not found? no one can explain?

file ts - 091.5°E - 3919 H 18385 - RTM SD5
_https://mega.nz/#!LVpSmBxB!mkmuMcFROXGSxfdECEMj3Nsq6LLo8xX0qkMhgLc9-TA
Program number 15 ECM key found
big record upload please
150 or 200 mb

satelitindonesia
Senior Member
- Messages
- 336
Program number 15 ECM key found
big record upload please
150 or 200 mb

yes, if use poc v.1 found ecm key but not success open :mecry:
satelitindonesia
Senior Member
- Messages
- 336
big record upload please
150 or 200 mb
this ts file
_https://mega.nz/#!nJpG0bJT!WV_0d6aH4FwOk4KBYusUBd769Y-CEdAKpA-zL1t5HzM
this emm raw
_https://mega.nz/#!3YQxQR4I!iOgaUI6PQ3L2eIzPodToy0C3pDW2NyuMl_jnhreLgdk
